
Welcome to SecureXplore, your gateway to the exciting world of cyber security. In this blog, we embark on a journey to explore the ever-evolving landscape of digital security, equipping you with the knowledge and tools to navigate this dynamic realm with confidence. Through our comprehensive articles, expert insights, and practical tips, we aim to empower individuals and businesses alike to fortify their defenses against cybercrime and Vulnerabilities.
Saturday, March 2, 2024
Home
Unlabelled
Advanced Cyber-Espionage Campaign Targets Middle Eastern and African Governments
Advanced Cyber-Espionage Campaign Targets Middle Eastern and African Governments
Privilege Escalation and Backdoor Access: CL-STA-0043 employs various methods to escalate privileges and gain persistent access to compromised environments. The threat actors utilize native Windows tools, such as "sticky keys" (sethc.exe), to bypass login requirements and establish a backdoor. They replace the sethc.exe binary or modify registry references to execute cmd.exe, providing an elevated command prompt shell for running arbitrary commands. Similar tactics using the Utility Manager (utilman.exe) have been previously documented by CrowdStrike.
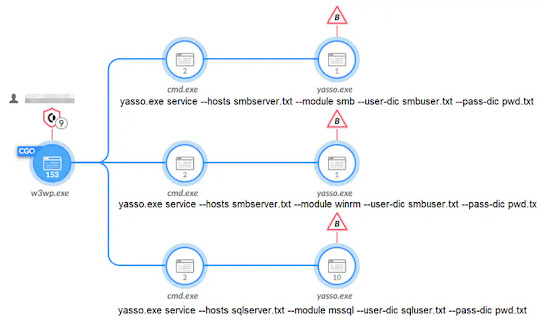
Innovative Techniques for Data Theft: In addition to leveraging Mimikatz for credential theft, the threat actors have employed novel methods for stealing passwords, lateral movement, and exfiltration of sensitive data. These techniques include executing a malicious DLL through network providers to harvest plaintext passwords and exporting them to a remote server. The attackers also utilize an open-source penetration testing toolset called Yasso to propagate across networks. Furthermore, they exploit the Exchange Management Shell and PowerShell snap-ins to gather emails of interest.
Attribution and Implications: The level of sophistication, adaptiveness, and victimology displayed by CL-STA-0043 strongly suggests the involvement of a highly capable APT threat actor, potentially operating on behalf of a nation-state. The campaign shares similarities with the activities of the Chinese state-sponsored group known as Silk Typhoon (formerly Hafnium), which targeted Microsoft Exchange Servers earlier this year. The ongoing attacks pose significant cybersecurity risks to governments in the Middle East and Africa and highlight the need for enhanced defensive measures and threat intelligence sharing.
Conclusion: The cyber-espionage campaign targeting Middle Eastern and African governments showcases the evolving tactics and capabilities of state-backed threat actors. The exploitation of vulnerabilities, advanced credential theft techniques, and exfiltration of sensitive data emphasize the importance of robust cybersecurity strategies and proactive defenses. Governments and organizations must remain vigilant, adopt best security practices, and collaborate to mitigate the risks posed by these sophisticated cyber threats.
Subscribe to:
Post Comments (Atom)
TOYOTA Data Breach – Hackers Group Leaked 240 GB of Sensitive Data Online
The US subsidiaries of Toyota Motor Corporation has reportedly fallen victim to a massive data theft, with around 240GB of confidential in...

Post Top Ad
Your Ad Spot
Author Details
Ut wisi enim ad minim veniam, quis nostrud exerci tation ullamcorper suscipit lobortis nisl ut aliquip ex ea commodo consequat. Duis autem vel eum iriure dolor in hendrerit in vulputate velit esse molestie consequat.
Powered by Blogger.
About Me
Search This Blog
Blog Archive
- August 2024 (2)
- April 2024 (1)
- March 2024 (17)
-
The US subsidiaries of Toyota Motor Corporation has reportedly fallen victim to a massive data theft, with around 240GB of confidential in...
-
Cybersecurity experts have revealed a significant hardware vulnerability—a backdoor—within specific models of MIFARE Classic contactless c...
-
AT&T has confirmed a data breach impacting 73 million current and former customers, despite initially denying that the leaked data origi...
-
Caesars Entertainment Inc. has reportedly paid a substantial sum to hackers who successfully infiltrated the company's systems and iss...
-
The recently established Rhysida ransomware group has claimed responsibility for the cyberattack on Maryland's Prince George's Cou...

.JPG)








No comments:
Post a Comment